How To Identify and Mitigate Cybersecurity Risks at Your Dealership

According to Cybersecurity Ventures, by 2025, cybercrime is expected to cost the world $10.5 trillion. But financial loss is not the only significant damage that cybercrime and cybersecurity risks can cause individuals and organizations.
A cyber-attack on a dealership can have severe consequences, such as disruptions to business operations, data breaches, damage to your dealership’s reputation, regulatory fines or legal penalties, intellectual property theft, and more.
Given these risks, it is crucial for dealerships to have proactive and retroactive cybersecurity measures in place to help mitigate cybersecurity risks. In this blog post, with insights from David Darrell, Director of Cloud Operations at IDS and over 25 years of IT experience, we explore how to identify and minimize cybersecurity risks at your dealership.
Click to Jump Ahead:
- What are the top cybersecurity risks my dealership faces?
- What type of information do hackers want from my dealership?
- Who is accountable for cybersecurity at my dealership?
1. Top Cybersecurity Risks: Malware & Social Engineering
Malware and social engineering tactics are two common methods used by hackers to gain unauthorized access to a dealership’s systems and data.
What is Malware?
According to McAfee, malware is “a catch-all term for any type of malicious software designed to harm or exploit any programmable device, service or network.”
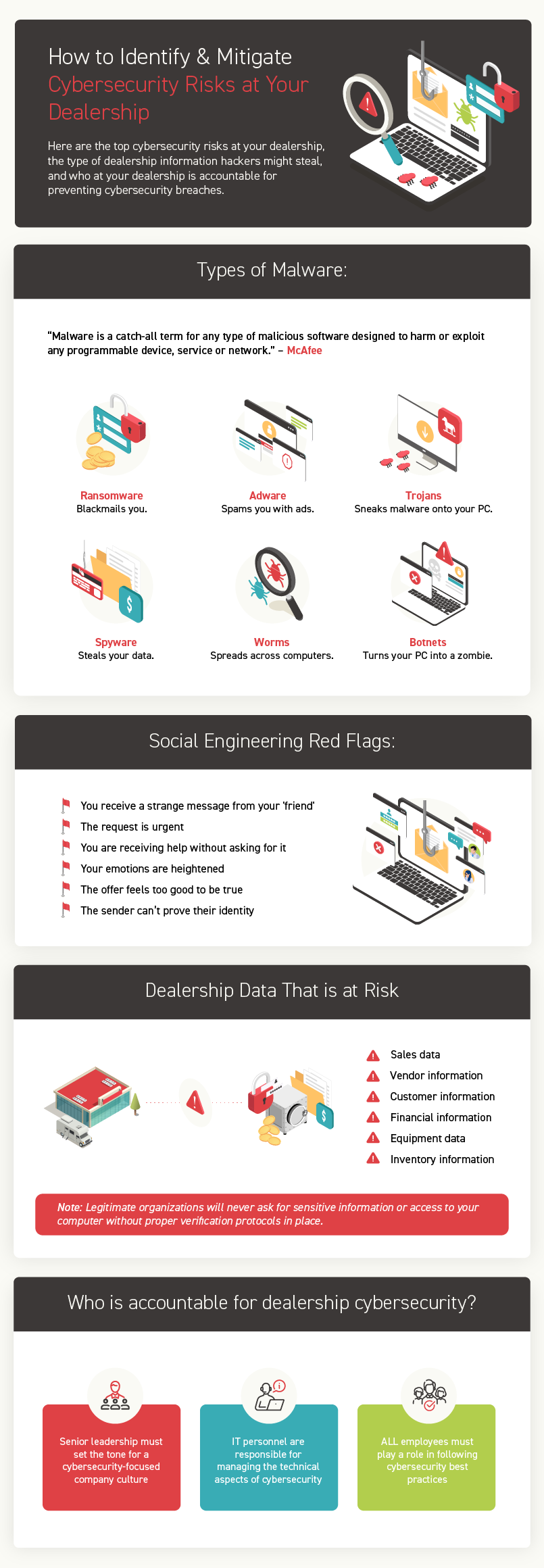
Each type of malware has its own specific characteristics and methods of attack, such as spyware, worms, Trojans, and botnets. These terms are defined below.
Ransomware – Blackmails You
Ransomware encrypts files on a victim’s computer, making it inaccessible until a ransom is paid. Oftentimes, the attackers will demand payment in the form of cryptocurrency to avoid detection. Even if the ransom is paid, it is not guaranteed that the files will be restored.
Spyware – Steals Your Data
This type of malware collects information from a victim’s computer without their knowledge. The information could be sensitive personal or financial data, such as credit card numbers or login credentials.
Adware – Spams You with Ads
Adware displays unwanted ads on a victim’s computer, which are often intrusive and lead the victim to click on them unintentionally. Clicking the ad potentially exposes the victim’s computer to additional forms of malware.
Worms – Spreads Across Computers
As self-replicating malware, worms spread over networks and computers via vulnerabilities in software or hardware. Once infected, worms can spread to other computers on a shared network, causing extensive damage to that network.
Trojans – Sneaks Malware Onto Your PC
Malware Trojans disguise themselves as legitimate programs with malicious code inside. They can perform a variety of malicious actions once downloaded and installed, including stealing information, deleting files, or granting remote access to the victim’s computer.
Botnets – Turns Your PC Into a Zombie
A botnet is a network of infected computers controlled by a single attacker called the botmaster. Infected computers are known as bots or zombies and can be abused for a variety of reasons, from launching DDoS attacks, stealing information, or sending spam emails. Oftentimes, victims are unaware that their computer has been infected and is part of a botnet.
What Are Social Engineering Tactics?
There are a variety of social engineering tactics that cyber attackers use to obtain a dealership’s data. Specifically, social engineering tactics manipulate individuals into giving away sensitive information or taking an action to the detriment of a dealership’s security.
Knowing which red flags to watch out for will prevent your dealership and your team members from becoming victims of an attack.
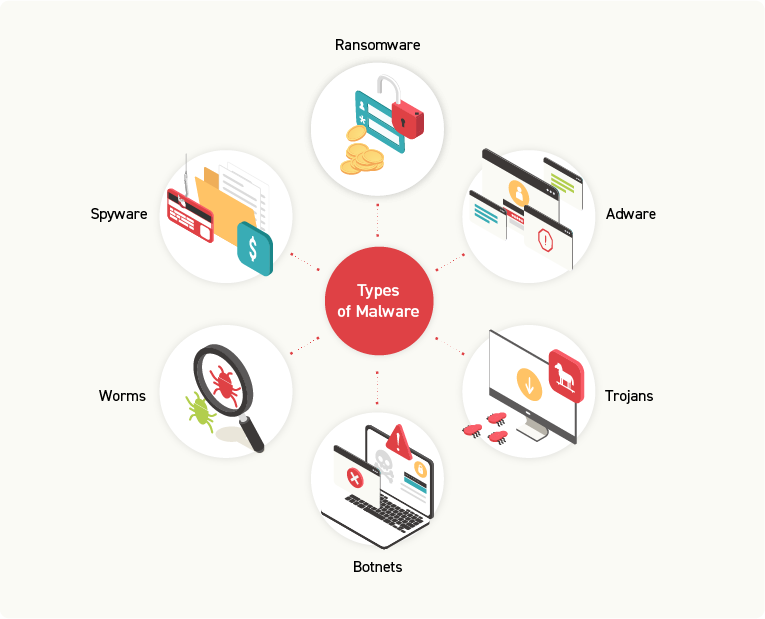
Social Engineering Red Flags:
You receive a strange message from your ‘friend:’
The hacker impersonates a friend or acquaintance, often over social media or email, and sends a message containing a strange link or attachment. If the recipient believes the message was sent by someone they know, they may click the link or download the attachment, which could contain malware.
Your emotions are heightened:
A social engineering attack typically takes advantage of emotions such as fear, curiosity, or greed. For example, the request might ask you to join an investment opportunity promising high returns.
The request is urgent:
The purpose of this tactic is to create a sense of urgency so that the victim feels compelled to act immediately.
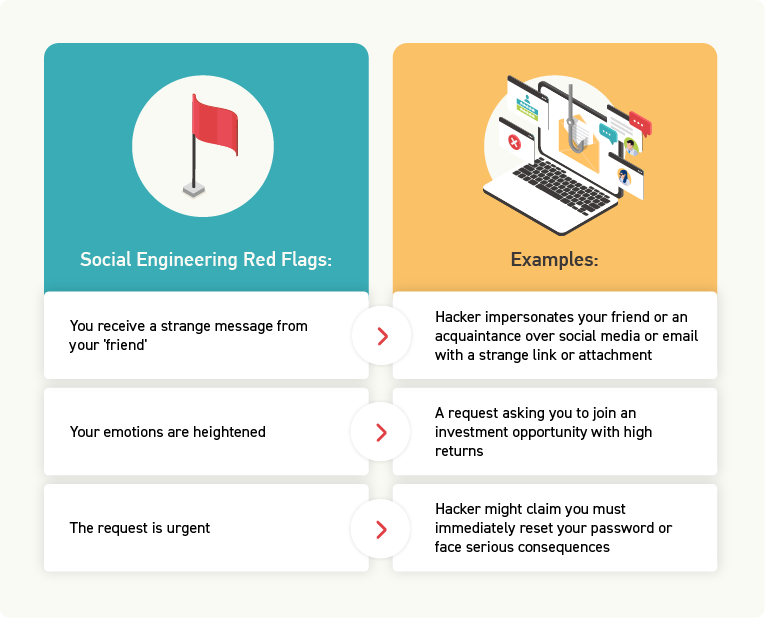
The offer feels too good to be true:
The victim is often lured by an offer that sounds enticing. But, in fact, the offer is just a ploy to get them to provide personal information or to download malware.
You receive help without asking for it:
The hacker pretends to be someone else, often an IT technician or customer service representative, who claims to have detected a problem with the victim’s computer or account. Hackers may ask victims to download a tool or grant remote access to their computers to install malware or steal sensitive information.
The sender can’t prove their identity:
Hackers often impersonate employees of legitimate organizations such as banks, government agencies, or well-known companies and use that to gain the trust of their victims. If the victim asks for proof of the sender’s identity, the hacker may provide a fake ID or document to gain the victim’s trust.
NOTE: Legitimate organizations will never ask for sensitive information or access to your computer without proper verification protocols in place.
2. Where Are There Cybersecurity Risks At My Dealership?
A dealership contains a lot of sensitive information within every department that a hacker would want to obtain access to. Here are some examples of the type of information that a hacker would want to steal from your dealership:
Sales data: this includes information such as pricing and profit margins which can be used by competitors or other malicious actors to gain an unfair advantage in the market
Vendor information: This could include the names and contact information of vendors, as well as details about the products or services they provide and the terms of their contracts with the dealership. A hacker could use the information to create fake invoices or payment requests
Customer information: customer names, addresses, phone numbers, and email addresses can all be used to carry out identity theft or targeted phishing attacks
Financial information: customers’ financial information such as credit cards, bank account information, financing agreements including loans and leases, and Social Security numbers. However, a hacker can use the dealership’s own financial reports to carry out financial crimes.
Equipment data: the service department has access to equipment data, such as repair histories and diagnostic information, which could be used to gain insight into the dealership’s operations
Inventory information: the parts department has information about the dealership’s inventory, such as types of parts, quantities, and prices which could be used to carry out fraudulent transactions.
Evidently, your dealership has a lot of data on hand. You use data to:
- Target and acquire new customers
- Sell and service specific things to customers
- Retain and possibly increase products and services adopted by your customers
Your dealership uses an abundance of technologies that store and process data, including mobile phones, tablets, and computers. Even though these tools make it easier to run your dealership, you shouldn’t overlook or minimize the importance of investing time and money into your dealership’s cybersecurity measures.
What if I don’t have the time or money for cybersecurity?
Ask yourself this: What will it cost if I don’t act?
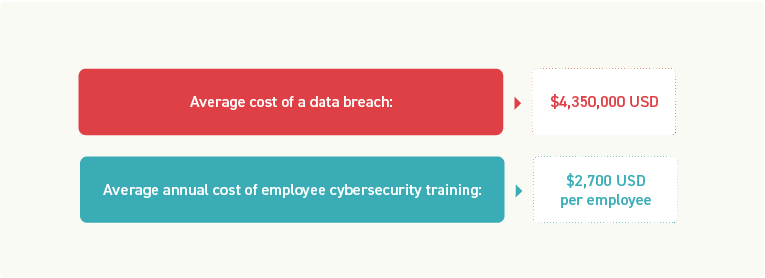
According to Statista, in 2022, the global average cost of one data breach was $4,350,000 USD.
By contrast, the average cost for cybersecurity-related training annually is $2,700 USD per employee.
As a rule of thumb, companies should spend about 10% of their IT budget on cybersecurity, including employee training.
3. Who Is Accountable For Cybersecurity And Cybercrime Risks At My Dealership?
Cybersecurity is the responsibility of everyone at a dealership. It’s a team effort and requires that all dealership employees work together to monitor and identify potential threats.
In addition to a financial commitment, there also needs to be a shift in corporate culture.
You must be willing to prioritize cybersecurity as a core part of your dealership’s business strategy, beginning with a commitment from senior leadership to educate all employees on the importance of cybersecurity.
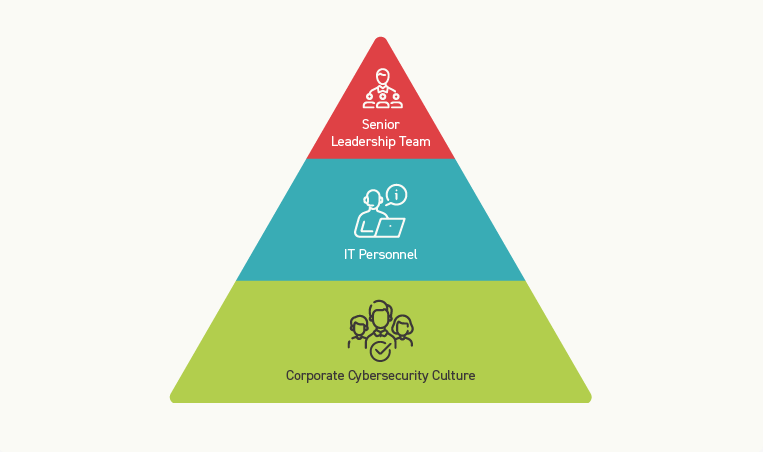
Senior leadership must set the tone for a cybersecurity-focused company culture and provide the necessary resources and support for implementing effective cybersecurity measures.
Your IT team is responsible for managing the technical aspects of cybersecurity, such as implementing firewalls, monitoring networks for suspicious activity, and managing user access to systems.
However, all employees must also play a role in preventing attacks by following best practices for password management, being cautious of suspicious emails and phone calls, and reporting any potential security threats.
This culture will require ongoing commitment, education, and investment. But ultimately, it will help your dealership to build customer trust and reputation, stay ahead of evolving threats, and ensure compliance with regulatory requirements around data privacy and security.
Protect Your Dealership’s Data With IDS Cloud
Cloud hosting provides several security benefits that can help protect against cyber-attacks, including encryption of data at rest and in transit, multi-factor authentication, and access controls.
With cloud hosting, a dealership’s data is securely stored in data centers that are maintained and monitored by the cloud service provider.
One significant advantage of cloud hosting is that it provides continuous monitoring and threat detection. Cloud service providers have teams dedicated to monitoring their systems for any unusual activity, including attempts to access data from unauthorized sources or patterns of behavior that suggest a cyber-attack. If any suspicious activity is detected, the provider can take immediate action to stop the attack and prevent further damage.
In combination with the proper employee training, cloud hosting can be a critical part of a dealership’s cybersecurity strategy.
David Darrell is director of Cloud Operations at Integrated Dealer Systems, an RV, marine and trailer dealership software provider.
